PENETRATION TESTING MADE PROACTIVE, POWERFUL, & PROVEN
Penetration testing simulates real-world cyberattacks to identify and fix security vulnerabilities in systems. It helps organisations strengthen defences and reduce the risk of breaches.



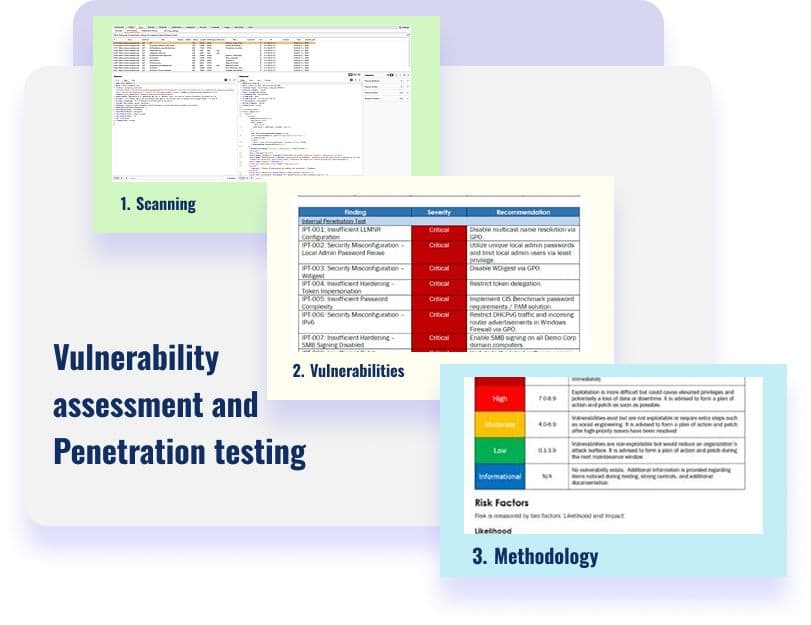
Why Accorp for Real-World Penetration Testing?
Accorp delivers expert-driven penetration vulnerability testing to help you find penetration testing vulnerabilities before attackers do. Fast, precise, and aligned with our VAPT testing process, we make security proactive, not reactive.
Proactive Over Reactive
Accorp prioritises proactive defence by identifying vulnerabilities long before attackers can exploit them, helping organisations avoid costly disruptions, reputational damage, and emergency remediation efforts.
Business-Aligned Security
Accorp aligns every penetration test with your business goals—ensuring security improvements deliver measurable ROI, support compliance, and strengthen the systems that matter most to your operations.
No Surprises, Ever
From scoping to reporting, Accorp maintains complete transparency with a clearly defined process, consistent communication, and zero unexpected add-ons, delays, or unclear findings.
Efficient & Cost-Effective
Accorp delivers high-quality, thorough penetration testing using proven methodologies, ensuring maximum value while keeping your teams, systems, and operations running smoothly.
Consultative Approach
Accorp's experts work closely with your team, offering guidance before, during, and after testing—ensuring you understand every risk, recommended fix, and long-term security implication.
Expert Insight That Drives Action
Accorp provides detailed, easy-to-understand reports backed by deep technical expertise, complete with prioritised remediation steps, impact analysis, and recommendations your team can act on immediately.
Accorp's Roadmap to Risk-Ready Penetration Testing
Our proven 8-step methodology ensures comprehensive security testing with minimal business disruption
Free Consultation
We assess your current security posture and answer questions about our penetration & vulnerability tester team and methods.
Pre-Engagement Questionnaire
You identify systems and assets in scope, including apps or APIs you'd like us to check my api or conduct an api free test on.
Scope Agreement
A tailored Statement of Work defining boundaries, tools like pentest scanner, and timelines.
Project Scheduling
We assign a dedicated manager to streamline communication and expectations.
Pre-Kickoff Call
We confirm everything—from access to readiness—a week before testing begins.
Testing Phase
We run real-world attacks using OWASP standards (penetration testing OWASP Top 10) and tools like pentest websites online, while keeping you updated routinely.
Reporting & Readout
You get reports in detail—with business impact, remediation steps, and follow-up strategies.
Retesting
Once fixes are applied, we validate and re-evaluate your setup through the same lens to confirm closure.
Types of Penetration Testing
Comprehensive security testing across all attack vectors and platforms
API Testing
We identify dangerous flaws in your APIs, supporting platforms that allow you to check my api health and security.
Network Layer Testing
Covers misconfigurations, access issues, and outdated services.
Mobile Application Testing
Android and iOS platforms tested using tools and methods similar to api free test platforms.
Web Application Testing
Tested against top known issues, including XSS and SQLi, using methods like penetration testing OWASP Top 10 and tools similar to pentest websites online.
Wireless Network Testing
Find unauthorised sniffing, rogue networks, encryption leakage, etc.
Facility Penetration Testing
Simulate real-world physical security breaches to assess access control and monitoring gaps.
Related Security Services
Vulnerability Assessment
Automated scanning to identify security vulnerabilities in your systems
Learn MoreSOC 2 Compliance
Demonstrate your commitment to security, availability, and confidentiality
Learn MoreISO 27001 Certification
Achieve international information security management system certification
Learn More